Various European customers of different banks are being targeted by an Android banking trojan called SpyNote as part of an aggressive campaign detected in June and July 2023.
“The spyware is distributed through email phishing or smishing campaigns and the fraudulent activities are executed with a combination of remote access trojan (RAT) capabilities and vishing attack,” Italian cybersecurity firm Cleafy said in a technical analysis released Monday.
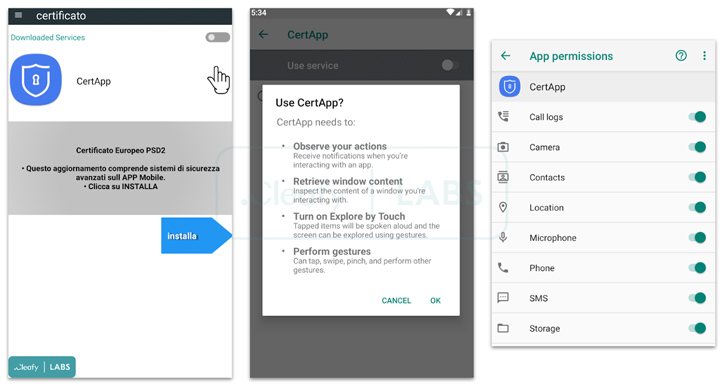
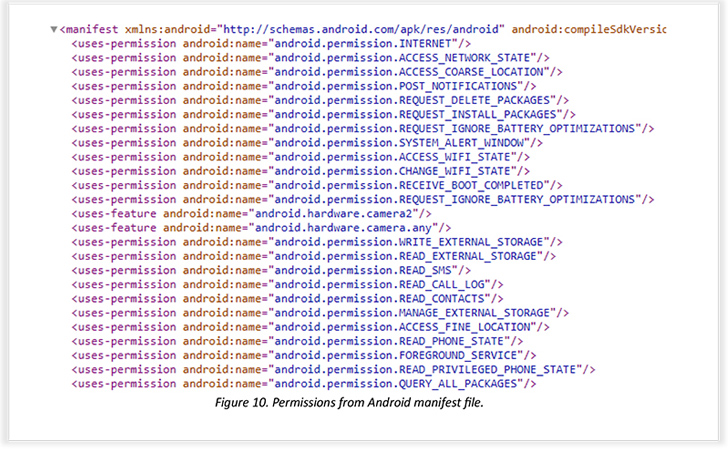
SpyNote, also called SpyMax, is similar to other Android banking Trojans in that it requires Android’s accessibility permissions in order to grant itself other necessary permissions and gather sensitive data from infected devices. What makes the malware strain notable is its dual functions as spyware and perform bank fraud.

The attack chains commence with a bogus SMS message urging users to install a banking app by clicking on the accompanying link, redirecting the victim to the legitimate TeamViewer QuickSupport app available on the Google Play Store.
“TeamViewer has been adopted by several [threat actors] to execute fraud operations through social engineering attacks,” security researcher Francesco Iubatti said. “In particular, the attacker calls the victim, impersonating bank operators, and performs fraudulent transactions directly on the victim’s device.”
The idea is to use TeamViewer as a conduit to gain remote access to the victim’s phone, and stealthily install the malware. The various kinds of information harvested by SpyNote include geolocation data, keystrokes, screen recordings, and SMS messages to bypass SMS-based two-factor authentication (2FA).
The disclosure comes as the hack-for-hire operation known as Bahamut has been linked to a new campaign targeting individuals in the Middle East and South Asia regions with the goal of installing a dummy chat app named SafeChat that conceals an Android malware dubbed CoverIm.
Delivered to victims via WhatsApp, the app houses identical features as that of SpyNote, requesting for accessibility permissions and others to collect call logs, contacts, files, location, SMS messages, as well as install additional apps and steal data from Facebook Messenger, imo, Signal, Telegram, Viber, and WhatsApp.

Cyfirma, which uncovered the latest activity, said the tactics employed by this threat actor overlap with another nation-state actor known as the DoNot Team, which was recently observed utilizing rogue Android apps published to the Play Store to infect individuals located in Pakistan.
While the exact specifics of the social engineering aspect of the attack is unclear, Bahamut is known to rely on fictitious personas on Facebook and Instagram, pretending to be tech recruiters at large tech companies, journalists, students, and activists to trick unwitting users into downloading malware on their devices.
“Bahamut used a range of tactics to host and distribute malware, including running a network of malicious domains purporting to offer secure chat, file-sharing, connectivity services, or news applications,” Meta revealed in May 2023. “Some of them spoofed the domains of regional media outlets, political organizations, or legitimate app stores, likely to make their links appear more legitimate.”