Security experts advise creating strong, complex passwords to protect our online accounts and data from savvy cybercriminals. And “complex” typically means using lowercase and uppercase characters, numbers, and even special symbols. But, complexity by itself can still open your password to cracking if it doesn’t contain enough characters, according to research by security firm Hive Systems.
In this article, we look into how long it would take for hackers to crack different types of passwords and what you can do to make them more secure.
How long does it take to crack a password?
In their 2024 Hive Systems Password Table report, Hive found that a complex, eight-character password that contains numbers, symbols, and both upper and lowercase letters will take seven years to crack — if an attacker were to use a top-of-the-line 12 x RTX 4090 graphics card.
In comparison, a five-character password with only upper and lowercase letters can be cracked in two minutes. Further, Hive says that a four-character password with only lowercase letters can be hacked instantly, while a five-character password with both upper and lowercase letters can be hacked in three seconds.
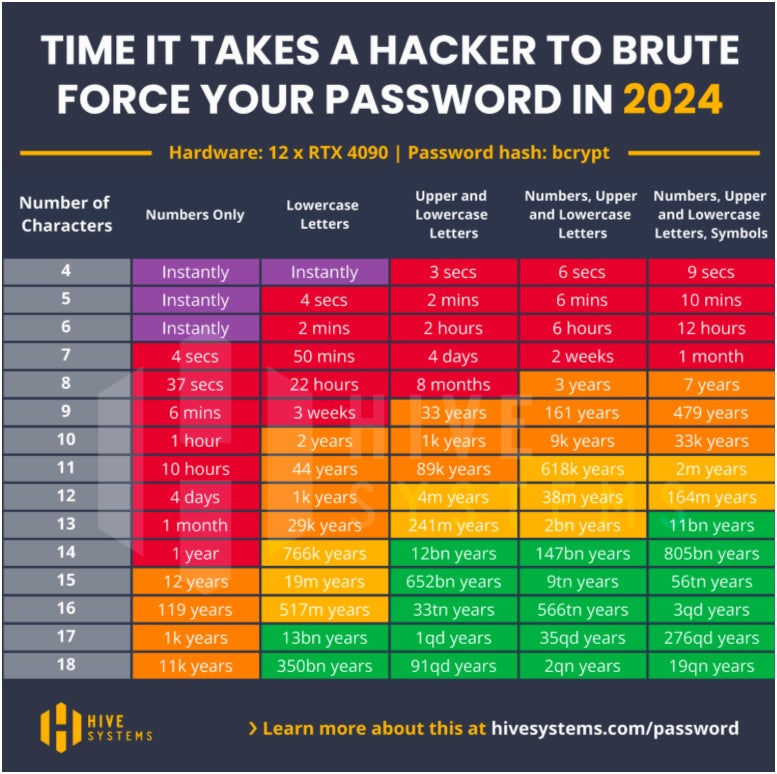
In my view, this shows how crucial it is to apply password best practices, such as using a mix of letters, symbols, and numbers, whenever possible. This is especially so since, given the stark contrast in the amount of time passwords could be cracked depending on their complexity.
On the plus side, even simpler passwords with a greater number of characters are less vulnerable to cracking in a short amount of time, according to Hive’s research. For example, a 10-character password made up of numbers would take one hour to crack. Meanwhile, upping that number-only password to 18 characters will increase the time frame to 11,000 years.
Looking into words versus numbers, Hive’s data shows that passphrases win over more traditional passwords. An 18-character password with only numbers would require 11,000 years to crack, but one with the same number of characters using lowercase letters would take 350 billion years to crack. This piece of data shows why passphrases, which use a long string of real but random words, can be more secure than a complex but short password.
Hive’s report shows that passphrases with a mix of 18 uppercase and lowercase letters, numbers, and symbols are the most difficult to brute force.
What tools do hackers use to crack your passwords?
A hacker aiming to crack complex yet short passwords quickly enough would need the latest and most advanced graphics processing technology. The more powerful the graphics processing unit, the faster it can perform such tasks as mining cryptocurrencies and cracking passwords.
With these GPUs, hackers can initiate brute-force attacks and use password-cracking software to guess your passwords and other credentials. Brute force attacks involve using GPUs and machine-powered trial and error in an attempt to get the right combination of characters, numbers, and symbols and, eventually, crack a user’s password.
For example, one of the top GPUs around today is Nvidia’s GeForce RTX 4090, a product that starts at $1,599. But even less powerful and less expensive GPUs can crack passwords of a small length and low complexity in a relatively short amount of time.
Hackers who don’t have the latest and greatest graphics processing on their computers can easily turn to the cloud, according to Hive. By renting computer and graphics hardware through Amazon AWS and other cloud providers, a cybercriminal can tap into multiple virtual instances of a powerful GPU to perform password cracking at a fairly low cost.
Plus, the advances in AI have given hackers another type of tool to crack passwords more quickly and efficiently. An April 2023 report from Home Security Heroes that analyzed 15,600,000 common passwords discovered that by using AI, hackers could crack 81% of them in less than a month, 71% in less than a day, 65% in less than an hour, and 51% in less than a minute.
SEE: Securing Linux Policy (TechRepublic Premium)
How to protect yourself and your organization from password cracking
Due to the progress in graphics and AI technology, most types of passwords require less time to crack than they did only two years ago. For example, a seven-character password with letters, numbers, and symbols would take seven minutes to crack in 2020 but only four seconds in 2023. Given these technological advances, how can you and your organization better secure your password-protected accounts and data? Here are a few tips.
Try using a passphrase instead of a password
A passphrase is a long string of often random words. Passphrases are often more secure than passwords and are usually easier to remember. Examples of this would be something like “Sunset-cola-Mouse!” or “GatePen2BoxerRose”.
If you go the passphrase route, there are a few things to remember:
- Make sure it’s at least 10-15 characters or more.
- Avoid using common phrases or song lyrics.
- Choose a passphrase that’s memorable to you.
- Add in some numbers and symbols to your phrases.
For a more in-depth tutorial, check out our What is a Passphrase? guide here.
Use a mix of numbers, symbols, uppercase, and lowercase letters at the same time
One of the main takeaways from the Hive Systems report is the significant influence complexity has on overall password strength. By complexity, I’m referring to the presence of letters (upper and lowercase), symbols, and numbers within passwords.
While having one character type makes your password more secure, having a mix of all of them will reap you the most benefits and security.
Use a password manager
Since creating and remembering multiple complex and lengthy passwords on your own is impossible, a password manager is your best bet. By using a password manager for yourself or within your organization, you can generate, store, and apply strong passwords for websites and online accounts.
Password managers to try out
1Password

If you want a password manager with a refined user interface, I recommend 1Password. 1Password has an intuitive and well-designed desktop application that will make it easy for both beginners and more advanced users to organize their passwords.
On top of that, their base 1Password subscription includes various additional security features, such as its Watchtower data breach scanner and secure password sharing and history capabilities. It’s also been independently audited by third-party firms, ensuring that it doesn’t record any user information as specified in their no-logs policy.
To learn more, check out our full 1Password review.
Bitwarden

For privacy enthusiasts, Bitwarden is my go-to pick. It’s an open-source password manager that makes its source code publicly available for review. This means that customers and interested parties can take a look at Bitwarden’s code and spot vulnerabilities themselves — providing a layer of transparency that’s crucial for a service which handles passwords. It also has one of the most generous free plans in the market, allowing free users to store an unlimited amount of passwords via an unlimited number of devices.
To learn more, check out our full Bitwarden review.
Keeper

If you want a more business-centric password manager, consider Keeper. With their business plan, you’re able to manage your team’s credentials through their admin console, team management functionality, and policy engine and enforcements feature. Their enterprise plan has even more team-related capabilities like AD and LDAP sync and SAML 2.0 authentication. I especially like Keeper’s built-in folders and subfolders system, enabling cleaner management of login credentials across teams and accounts.
To learn more, check out our full Keeper review.
This article was originally published in August 2023. It was updated by Luis Millares in January 2025.

